xNT NFC Chip
- NTAG216 13.56MHz ISO14443A & NFC Type 2 chip
- 2.1x12mm cylindrical sterile bioglass implant
- Want an analog? Check out the STL.
- Works with NFC smartphones and ISO4443A readers
- RFID Diagnostic Card and 13.56MHz X Field Detector included!
$25.00 – $60.00
More Details
WARNING This kit definitely contains dangerous things. While our x-series chip implants have undergone several quality checks during manufacture, and have been put through a battery of tests, they have not been certified by any government regulatory agency for implantation or use inside the human body. Use of this device is strictly at your own risk.The xNT NFC chip implant was designed by Dangerous Things and production of it was originally crowdfunded via an Indiegogo campaign in 2013. It works with NFC enabled smartphones, certain commercial access control systems, and USB contactless ISO14443A readers.
What can this chip implant do?
• Some types of access control applications
• Share data with NFC enabled smartphones
• Trigger events on NFC devices like smartphones
• Scan this chip implant to log into your computer
What this chip implant can’t do
• Can’t copy other chip IDs to this chip, ID is set
• Can’t make payments with this chip implant
• Chip implants can’t be used for GPS or tracking
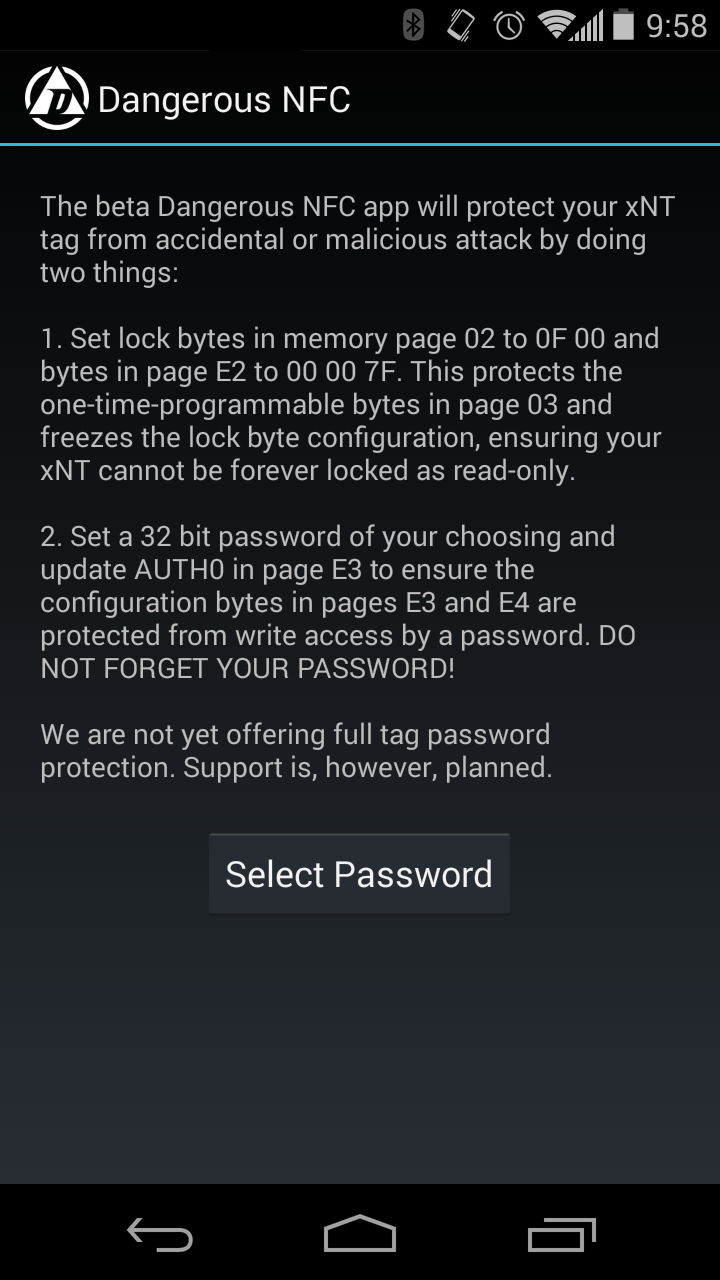
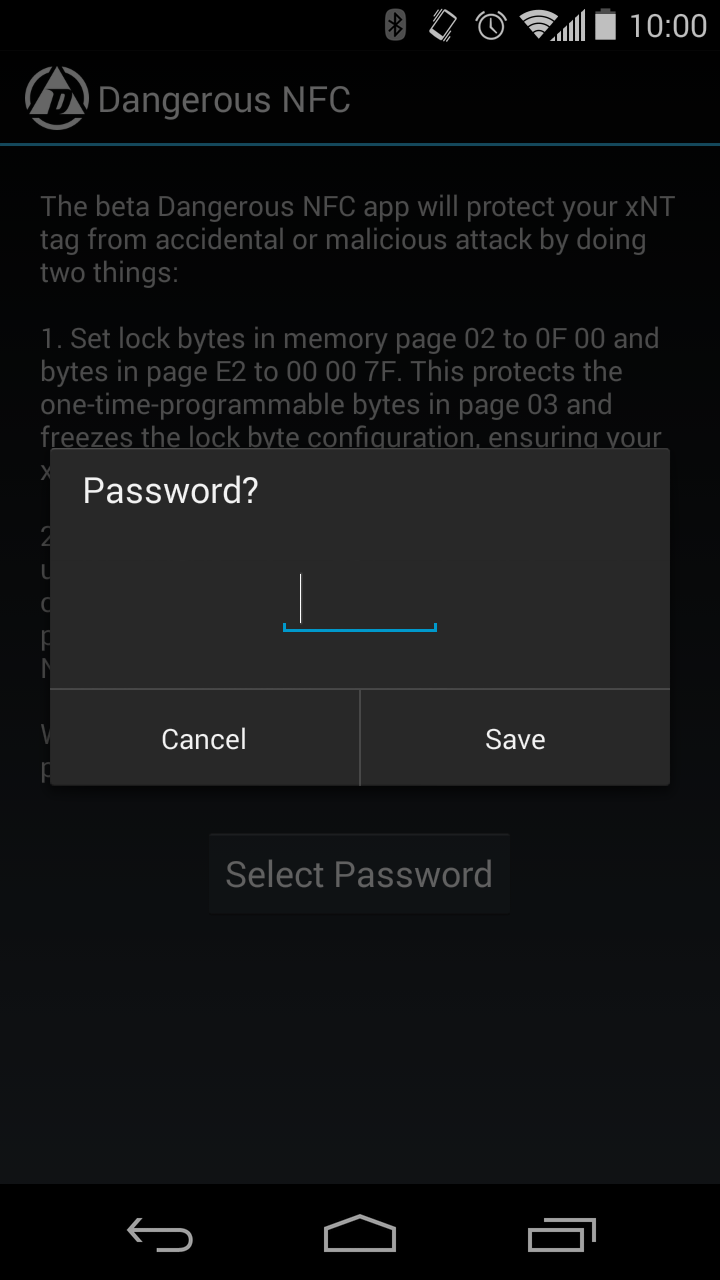
Important Things To Know
It’s going in your body, you should learn about things like performance expectations, installation procedure, first steps after installation, etc.
xNT Kit Contents
The xNT kit contains the following products and materials, which are designed to enable you to bring the kit to a professional installation partner for installation.
- 1 sterile injector assembly, pre-loaded with xNT chip implant
- 2 single use ChloraPrep antiseptic wipes
- 1 sterile gauze pad for post-installation wound care
- 1 sterile expandable-fabric adhesive bandage
- 1 pair of non-sterile, non-latex procedure gloves
xNT Kit Extras
The following accessories also come with the xNT kit. These accessories are “field detection” tools designed to assist you with identifying the type of readers you may encounter, but also the best location and orientation to present your xNT chip implant to any reader to get reliable performance.
- 1 RFID Diagnostic Card
- 1 13.56MHz X Field Detector
Our X Field Detectors (XFD) will show you the best position and orientation to present your chip implant to any readers of the same frequency, while our RFID Diagnostic Card will tell you all about the frequency and duty cycles of random readers you encounter in the wild.

 Passive RFID and NFC chips are batteryless, magnetically coupled devices that power themselves and communicate data over a shared magnetic field that the reader generates. This means their effective read range and performance depends entirely on how well the antenna coils of both the chip and reader couple with each other. This typically means the
Passive RFID and NFC chips are batteryless, magnetically coupled devices that power themselves and communicate data over a shared magnetic field that the reader generates. This means their effective read range and performance depends entirely on how well the antenna coils of both the chip and reader couple with each other. This typically means the 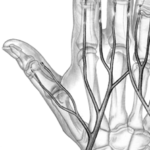 Our x-series transponders are typically installed into the webbing between the metacarpal bones of the index finger and thumb, resting parallel to the index metacarpal. They should be at least 5mm away from any bone or other implants to avoid possible impacts. The reason chip implants are usually installed in the hand has to do with the extremely short read range of most small chip implants. In the case of access control where the chip must be presented dirctly to a fixed reader of some kind, the hand is easily able to be properly positoned in front of the reader. To find out more about common installation locations of the hand, visit
Our x-series transponders are typically installed into the webbing between the metacarpal bones of the index finger and thumb, resting parallel to the index metacarpal. They should be at least 5mm away from any bone or other implants to avoid possible impacts. The reason chip implants are usually installed in the hand has to do with the extremely short read range of most small chip implants. In the case of access control where the chip must be presented dirctly to a fixed reader of some kind, the hand is easily able to be properly positoned in front of the reader. To find out more about common installation locations of the hand, visit  Achieving a safe installation definitely requires skill and experience performing aseptic procedures. Dangerous Things prefers our customers locate one of our
Achieving a safe installation definitely requires skill and experience performing aseptic procedures. Dangerous Things prefers our customers locate one of our